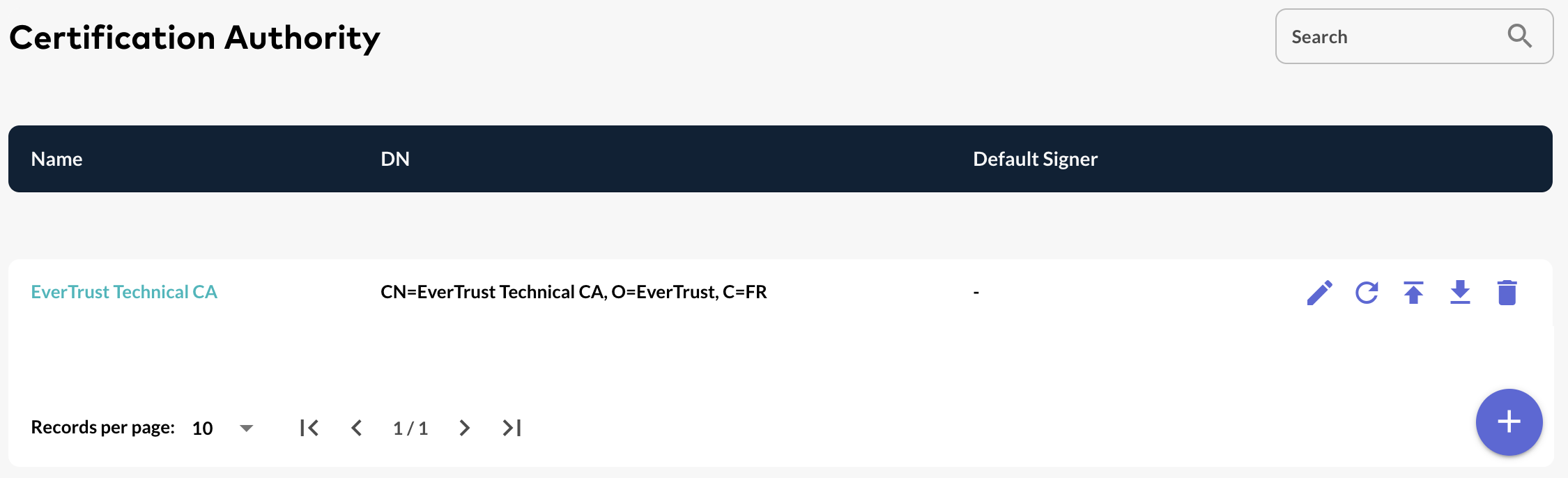
Importing a Certificate Authority
Step 1: Access the OCSPd Web Management Console;
Step 2: In the 'Configuration' left menu, select 'Certificate Authorities':
Step 3: In the Certificate Authorities page, hit the '+' button at the bottom of the page:

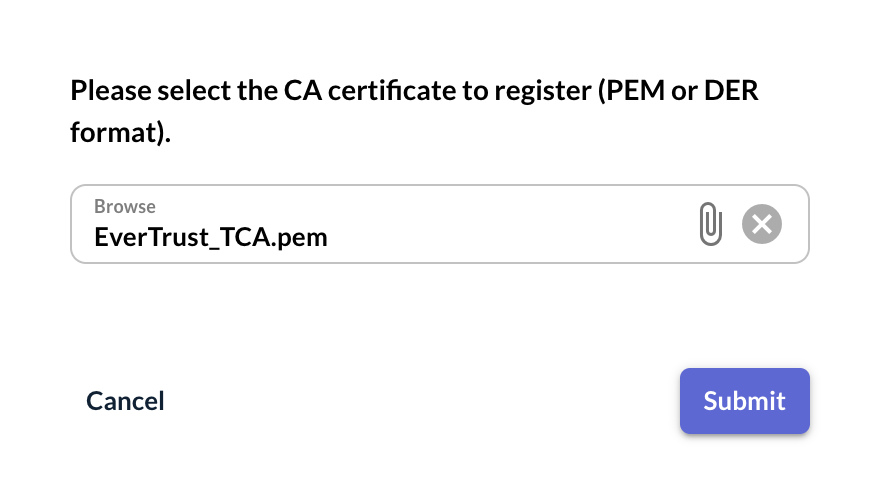
Step 4: Browse for the certificate of the Certificate Authority you are willing to load (PEM or DER) and hit the 'Submit' button:
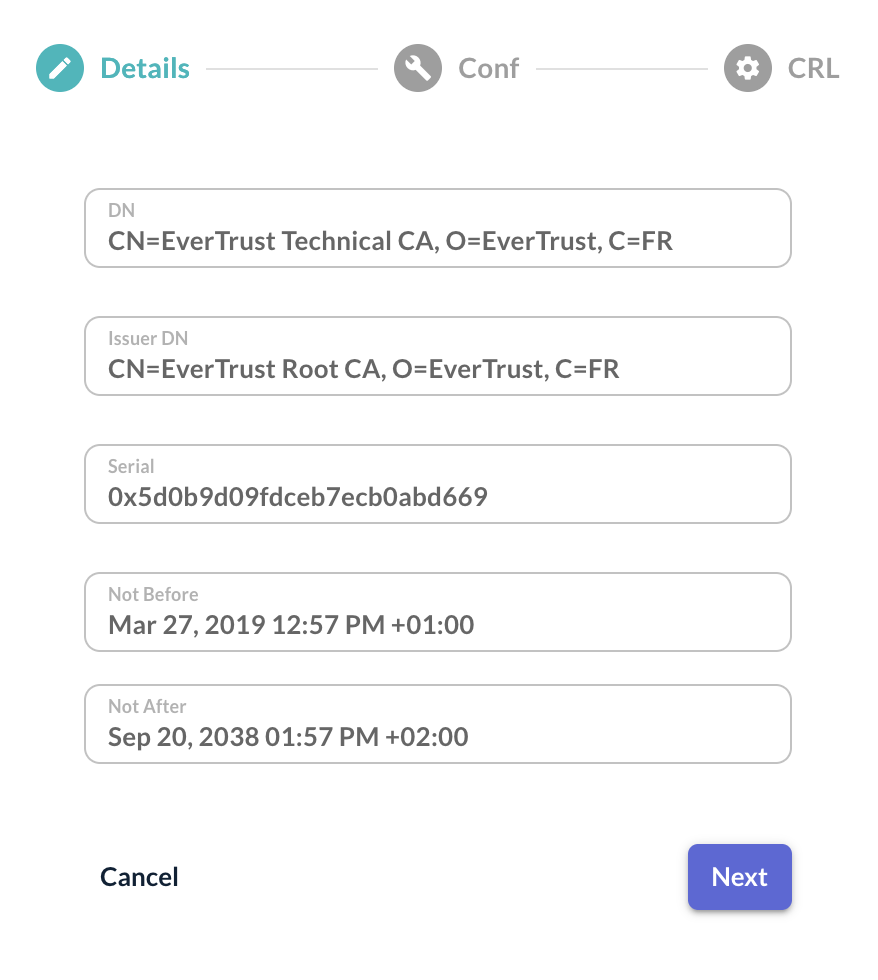
Step 5: The Certificate Authority is loaded and the details of the CA are displayed:
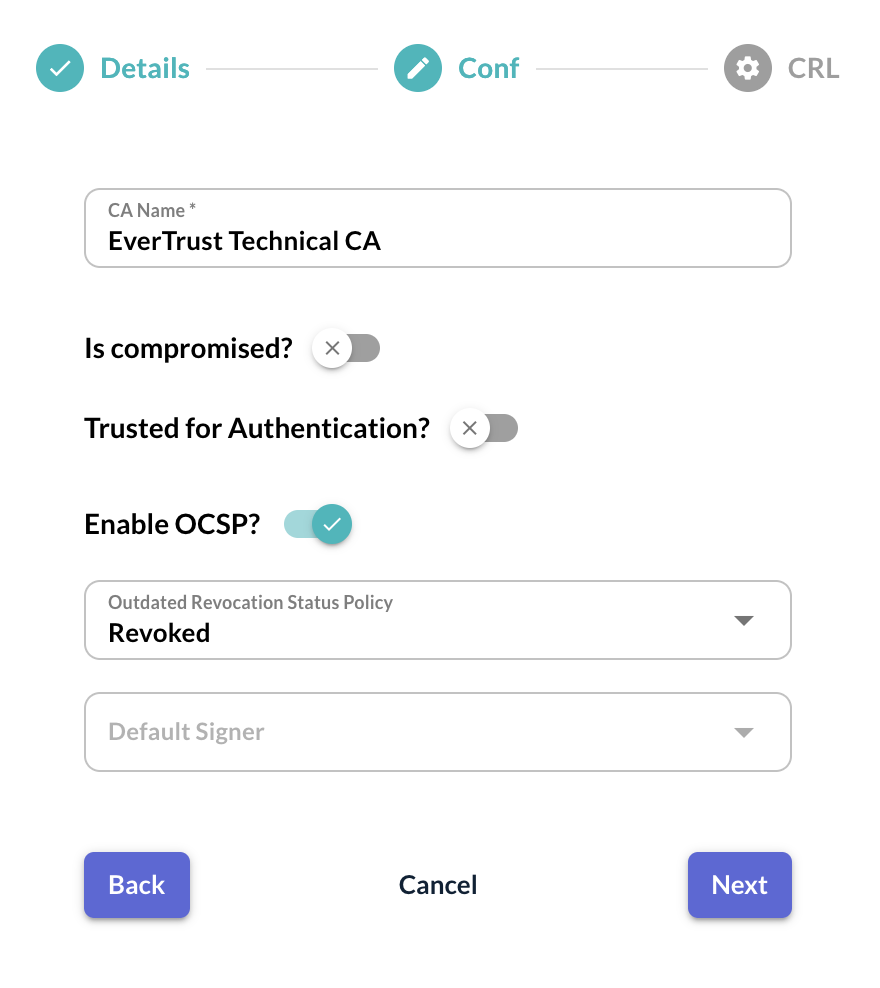
Step 6: Click on 'Next' and specify the following configuration information:
-
'Name': This is the name of the Certificate Authority within OCSPd;
-
'Is compromised?': If this parameter is checked, any OCSP request targeting tis Certificate Authority will trigger a 'revoked' response and the revocation date will be set as the request date;
-
'Trusted for Authentication?': If this parameter is checked, this Certification Authority is trusted for client certificate authentication on the OCSPd Web Management Console;
-
'Enable OCSP?': This parameter indicates if OCSPd should serve OCSP responses for this particular Certificate Authority;
-
'Outdated Revocation Status Policy': This defines the behavior of the OCSP responder when the revocation status is unavailable (CRL is expired or cannot be downloaded). OCSPd implements 3 policies:
-
'Revoked': any OCSP request will trigger a 'revoked response (RFC 5019 compliant);
-
'Unknown': any OCSP request will trigger an 'unknown' response;
-
'Last available status': the OCSP responder will determine the status based on the last information available (this policy is not compliant with the RFC 5019, but it allows avoiding denial of services when CRL is unavailable or expired);
-
-
'Default Signer': This parameter indicates which signer should be used to sign the OCSP responses for this particular CA when the responder to use is not defined in the URL.
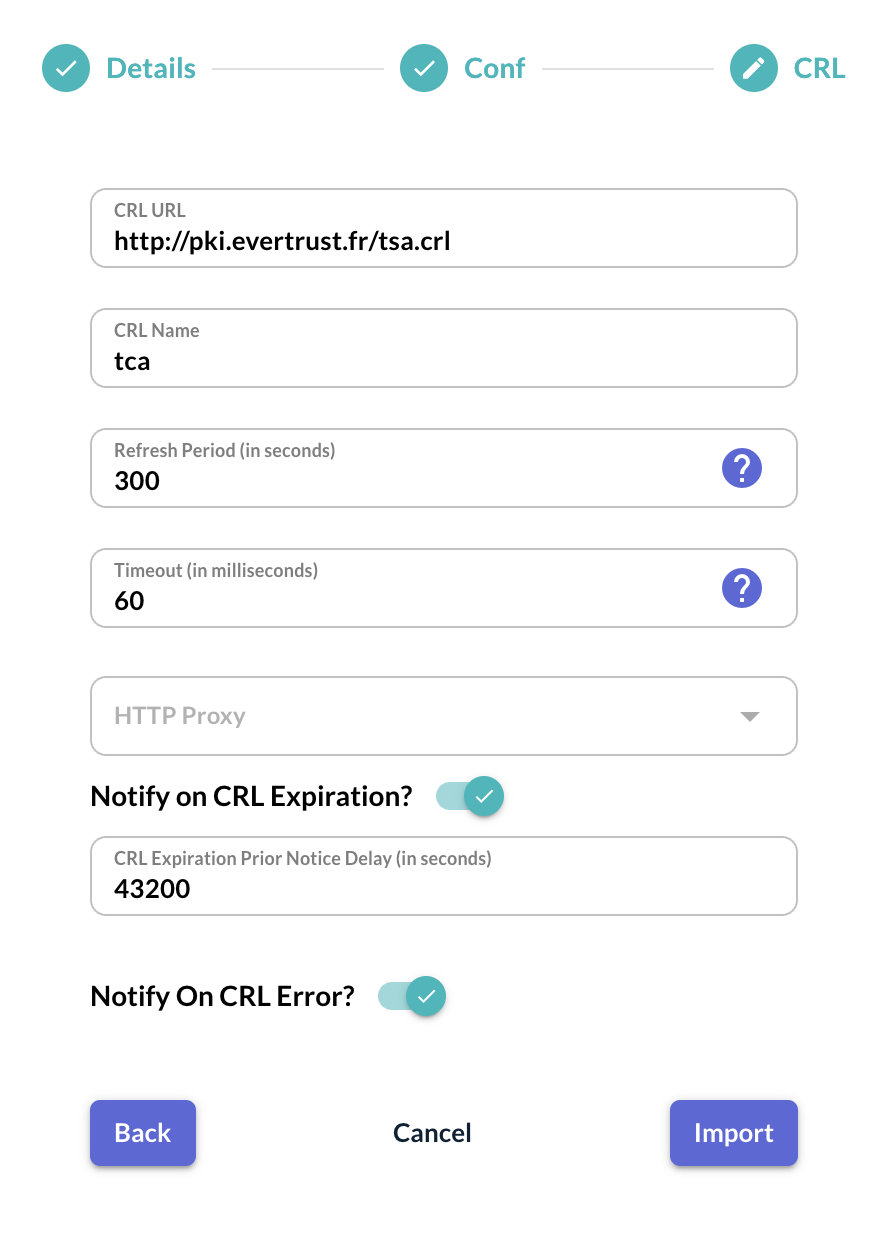
Step 7: Click on 'Next' and specify the following CRL configuration information:
-
'CRL URL': This is the URL where the CRL can be downloaded from. OCSPd currently supports HTTP and LDAP only;
-
'CRL Name': This parameter specifies how the CRL should be named when available through HTTP on the OCSPd component. For example, if the CRL name is configured as 'acsa', then, the CRL will be available under http://[EverTrustOCSP IP or DNS NAME]/acsa.crl (DER format) and http://[EverTrustOCSP IP or DNS NAME]/acsa.pem (PEM format). If the CRL Name parameter is not defined, the CRL will be name after the CA Name;
-
'Refresh Period': This parameter defines the CRL refresh period in seconds. For example, for a value of 300, OCSPd will attempt to download the CRL every 300 seconds, i.e. 5 minutes. If this parameter is set to '0', the CRL will not be downloaded at all;
-
'Timeout': This parameter defines the CRL timeout in milliseconds. If this parameter is set to '0', no timeout will be set;
-
'Proxy': This parameter defines the proxy to use to download the CRL. Proxies are declared in the 'Proxies' page;
-
'Notify on CRL expiration?': If this parameter is checked, an email will be sent to the Administrator when the CRL is expired;
-
'CRL Expiration Prior Notice Delay (in seconds)': This parameter defines the CRL expiration delay prior to notify the Administrator. For example, for a value of 43200, OCSPd will send an email to the Administrator 12 hours before the expiration of this Certification Authority CRL and each time the CRL is refreshed (defined by 'Refresh Period' parameter);
-
'Notify on CRL error?': If this parameter is checked, an email will be sent to the Administrator when the CRL retrieving of this Certification Authority will fail and each time the CRL is refreshed (defined by 'Refresh Period' parameter).
Step 8: Hit the 'Import' button:
Step 9: The Certificate Authority is successfully imported: