WCCE
Introduction
This section details how to configure and consume the Windows Client Certificate Enrollment (WCCE) protocol.
Managing certificate lifecycle through the WCCE protocol involves up to three components:
-
Active Directory asset (domain controller, server, workstation, user) as WCCE Client;
-
WinHorizon as the Active Directory enrollment service;
-
Horizon as the WCCE proxy;
| WCCE enrollment modes will be detailed later on. |
The protocol paradigm can be described as follows: 'every Windows Active Directory member (machines, users) can use DCOM interfaces to interact with a CA to request certificate enrollment'.
The following schema is a simplified workflow of an WCCE enrollment:
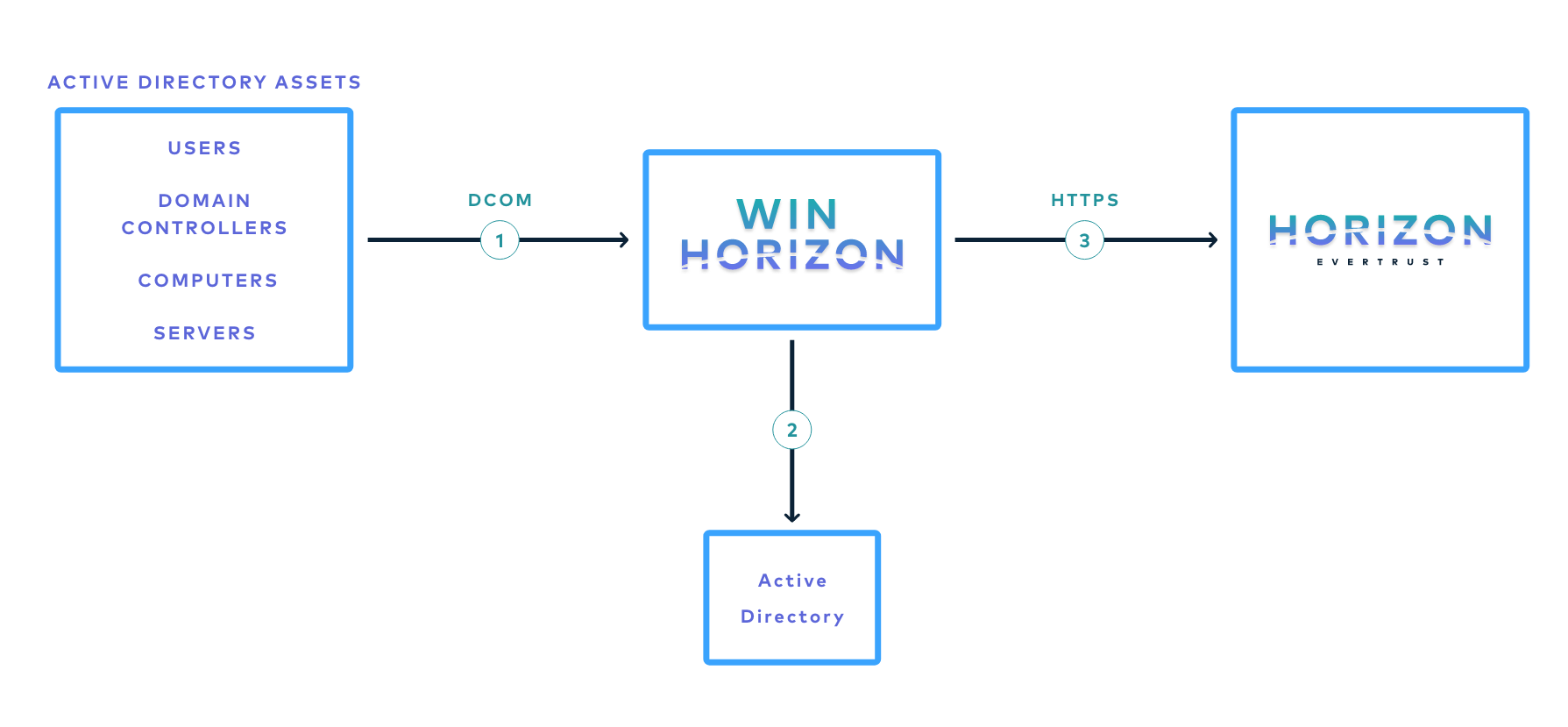 The protocol is based on the notion of Active Directory membership and configuration.
Active Directory clients (such as machines and users) having rights on Microsoft Certificate Templates can use Active Directory enrollment service through DCOM interface to request certificate enrollment.
The protocol is based on the notion of Active Directory membership and configuration.
Active Directory clients (such as machines and users) having rights on Microsoft Certificate Templates can use Active Directory enrollment service through DCOM interface to request certificate enrollment.
Horizon supports different WCCE enrollment modes:
-
Entity: Certificate’s elements are built using Active Directory content;
-
Enrollment On Behalf of Others (EOBO): Certificate signing request (CSR) is signed by one/many Certificate Enrollment Agent(s);
-
Trust request: Certificate signature request (CSR) content is fully trust and certificate will be created using its content.
| For Enrollment On Behalf of Others (EOBO) enrollment mode, it is possible to configure a whitelist of Authorized CAs trusted as issuers of enrollment agent certificates. |
Windows official resources
EverTrust WCCE implementation is based on official WCCE documentation provided by Microsoft:
Prerequisites
-
WinHorizon should be installed using WinHorizon installation guide;
-
WinHorizon and Active Directory should be configured using WinHorizon administration guide.
WCCE Forest
The first step is to register WCCE Forest on which you want to use WCCE protocol through Horizon.
How to configure WCCE Forest
1. Log in to Horizon Administration Interface.
2. Access WCCE Forest from the drawer or card: Protocol > WCCE > Forest.
3. Click on .
4. Fill the mandatory fields.
-
Forest Name* (string input): Enter the Active Directory forest name.
5. Click on the save button.
You can duplicate or delete
the WCCE Forest.
|
You won’t be able to delete an WCCE Forest if it is referenced somewhere else. |
WCCE Profile
The second step details how to create and configure a WCCE Horizon profile. This profile is an internal Horizon profile.
How to configure a WCCE Profile
1. Log in to Horizon Administration Interface.
2. Access WCCE Profile from the drawer or card: Protocol > WCCE > Profiles.
3. Click on .
4. Fill the mandatory fields.
General
-
Name* (string input):
Enter a meaningful profile name. It must be unique for each profile. Horizon uses the name to identify the profile. As the name will be part of an URL, it is advisable to use only lower case letters and dashes. -
Enabled* (boolean):
Indicates whether the profile is enabled or not. The default value is set to true. -
Max certificate per holder (int):
If specified, defines the maximum number of active certificates for a given Holder. If the number of active certificates exceeds this parameter, then the oldest certificate(s) above the limit will be automatically revoked. -
PKI (select):
Select a PKI connector previously created.
Self Permissions
-
Revoke (boolean):
Specify whether the certificate’s owner is authorized to revoke the certificate with no validation workflow. The default value is set to false. -
Request Revoke (boolean):
Specify whether the certificate’s owner is authorized to request the revocation of the certificate. The default value is set to false. -
Update (boolean): Specify whether the certificate’s owner is authorized to update the certificate with no validation workflow. The default value is set to false.
-
Request Update (boolean):
Specify whether the certificate’s owner is authorized to request certificate’s update. The default value is set to false. -
Recover (boolean):
Specify whether the certificate’s owner is authorized to recover the certificate with no validation workflow. The default value is set to false. -
Request recover (boolean):
Specify whether the certificate’s owner is authorized to request certificate’s recover. The default value is set to false.
You can further configure the profile using the Common configuration profile and Notification tabs.
5. Click on the save button.
You can edit , duplicate
or delete
the WCCE Profile .
|
You won’t be able to delete a WCCE Profile if this one is referenced somewhere else. |
WCCE Template Mapping
The third and last step is to configure mapping between Microsoft Certificate Template configured on Active Directory and Horizon WCCE profile. A mapping is created using a specific enrollment mode. As a result of this mapping, every Microsoft Certificate Template can issue certificate from different PKI (using PKI connector of WCCE profile associated to Microsoft Certificate Template).
How to configure WCCE Template Mapping
1. Log in to Horizon Administration Interface.
2. Access WCCE Forest from the drawer or card: Protocol > WCCE > Forest.
3. Identify the section corresponds to the forest for which you want to add mapping. Click on + button.
4. Fill the mandatory fields.
-
Microsoft Template Name* (string input):
Enter the Microsoft Certificate Template name created on Active Directory side. -
Enrollment mode (select):
Specify the enrollment mode of this mapping. -
EOBO CAs (select):
Specify the CA(s) to use for EOBO enrolment. -
Profile* (select):
Select a previously created WCCE profile.
5. Click on the save button.
You can edit or delete the WCCE Template mapping.
WCCE test enrollment
This section details how to use the Microsoft Management Console (MMC) to manually retrieve a certificate through WCCE using different enrollment modes. If you want to enroll machine certificate you need to perform the following actions using Administrator Account.
1. Launch mmc.exe
2. Click on File > Add/Remove or Remove Snap-ins
3. On the left panel, click on Certificates then Add
| If you don’t have administrative privileges, the User certificate store will be automatically chosen. If your account has administrative privileges, it will be prompted a window to choose Microsoft Certificate Store to use. If you want to enroll User certificate please chose My user account. If you want to enroll Machine certificate (computer or IIS for example) please chose Computer account. |
4. Navigate to Personal > Certificates
5. Right click on Windows and chose All tasks > Request certificate
6. Click on Next
7. On the next step, let default enrollment policy configuration, then click on Next
The next step lists all Microsoft Certificate Templates on which you have enrollment rights. The Microsoft Certificate template selection and last parts of this testing procedure are specific to the enrollment mode you want to perform.
Please refer to the proper section below.
Requesting a certificate using 'Entity' enrollment mode
8. Select the Microsoft Certificate Template configured on Horizon side as a part of a Template Mapping using Entity enrollment mode. Click on Next
9. Click on Enroll to request Enrollment.
10. Enrollment is requested to WinHorizon. Few seconds later, if enrollment is successful it will be displayed STATUS: Succeeded. Click on Finish.
11. Your certificate is displayed and available.
Requesting a certificate using 'Enrollment On Behalf of Others' enrollment mode
8. Identify the Microsoft Certificate Template configured on Horizon side as a part of a Template Mapping using Enrollment On Behalf of Others (EOBO) enrollment mode. Click on Details then Properties.
9. Navigate to Extensions tab and select Enrollment Agent Certificate (to be used to sign Certificate Request). Click on OK.
10. Click on Enroll to request Enrollment.
11. Enrollment is requested to WinHorizon. Few seconds later, if enrollment is successful it will be displayed STATUS: Succeeded. Click on Finish.
12. Your certificate is displayed and available.
Requesting a certificate using 'Trust request' enrollment mode
8. Identify the Microsoft Certificate Template configured on Horizon side as a part of a Template Mapping using Trust request enrollment mode. Click on Details then Properties.
9. Navigate to Subject tab to build your Certificate request manually. Click on OK.
10. Click on Enroll to request Enrollment.
11. Enrollment is requested to WinHorizon. Few seconds later, if enrollment is successful it will be displayed STATUS: Succeeded. Click on Finish.
12. Your certificate is displayed and available.
WCCE MSAD Connector
This section details how to to configure the Microsoft Active Directory Connectors.
How to configure an MSAD Connector
1. Log in to Horizon Administration Interface.
2. Access MSAD Connectors from the drawer or card: Protocol > WCCE > MSAD Connectors.
3. Click on .
4. Fill in the mandatory fields.
General
-
Name* (select):
Select the Active Directory Forrest you want to use to set up the connector. -
Hostname* (string input):
DNS name or IP of the Active Directory domain. -
Port (string input):
Port to connect to the Active Directory. The default value is set to 636. -
Proxy(select):
Select a proxy to connect to the Active Directory, if needed. -
Bind DN* (string input):
DN of the Active Directory account. Must have right privileges to browse and list objects. -
Password* (string input):
Password associated with aforementioned Active Directory DN account. -
Timeout* (finite duration):
The time before Horizon stop trying to connect to Active Directory. Must be in valid finite duration. -
Max stored certificate per holder (int):
When specified, define the maximum number of active certificates for a given Holder.
Assets identification
-
Base DN* (string input):
It can be the root of your domain or a restriction. -
LDAPPUB Filter (string input):
This filter must respect LDAPPUB filter syntax.
Actor management
These configuration elements mainly define the number of authorized interactions with the remote service on a defined period. For example, one needs to ensure that the remote service will not be requested more than 5 times per 3 seconds. Throttle parallelism defines the number of times and Throttle duration the period of time. Therefore, on the above example, throttle parallelism would be set to 5 and throttle duration would be set to 3 seconds.
-
Throttle duration* (finite duration):
The default value is set to 3 seconds. Must be a valid finite duration. -
Throttle parallelism* (int):
The default value is set to 3.
5. Click on the save button.
You can update or delete
the MSAD Connector.
|
You won’t be able to delete a MSAD Connector if this one is referenced somewhere else. |
WCCE Scheduled Tasks
This section details how to schedule tasks that will run periodically on your WCCE profiles. You will be able to use MSAD Connector to browse Active Directory and retrieve changes (basically computer removal) to trigger certificate revocation. This mechanism works using comparison between Active Directory content (using MSAD connector) and Horizon certificate list based on a specific WCCE profile. If Horizon has a certificate for a holder that does not exist on Active Directory side a revocation will be triggered automatically.
How to configure WCCE Scheduled Tasks
1. Log in to Horizon Administration Interface.
2. Access WCCE scheduled tasks from the drawer or card: Protocol > WCCE > Scheduled Tasks.
3. Click on .
4. Fill the mandatory fields.
-
WCCE Profile* (select):
Select the target WCCE profile. -
Target Connector* (select):
Select the MSAD connector to use as golden source of active Active Directory objects. -
Cron scheduling in Quartz format (cron expression):
Enter a Cron scheduling expression (in Quartz format). Default value is every 5 hours. -
Revoke (boolean):
If true, will revoke all certificate that do not exist on the AD side. -
Dry run (boolean):
If enabled, revocation actions will not be performed. Instead, a message will be logged, explaining what would have been done.
5. Click on the save button.
You can run , update
or delete
the Schedules Tasks.