Security
Tenancy
EVERTRUST Cloud provides a single-tenant architecture, meaning each instance is in-use by exactly one customer. However, some resources are shared in the cloud platform among multiple customers:
-
the database cluster holds multiple databases. Each instance authenticates to the database with a dedicated user which holds limited read and write rights to its own database. No instance can access other instances data.
-
the workloads Kubernetes clusters hosts multiple workspaces. Each workspace has a dedicated namespace, which has strict firewall policies preventing communication with other namespaces. All instances within one namespace will however be able to communicate with each other.
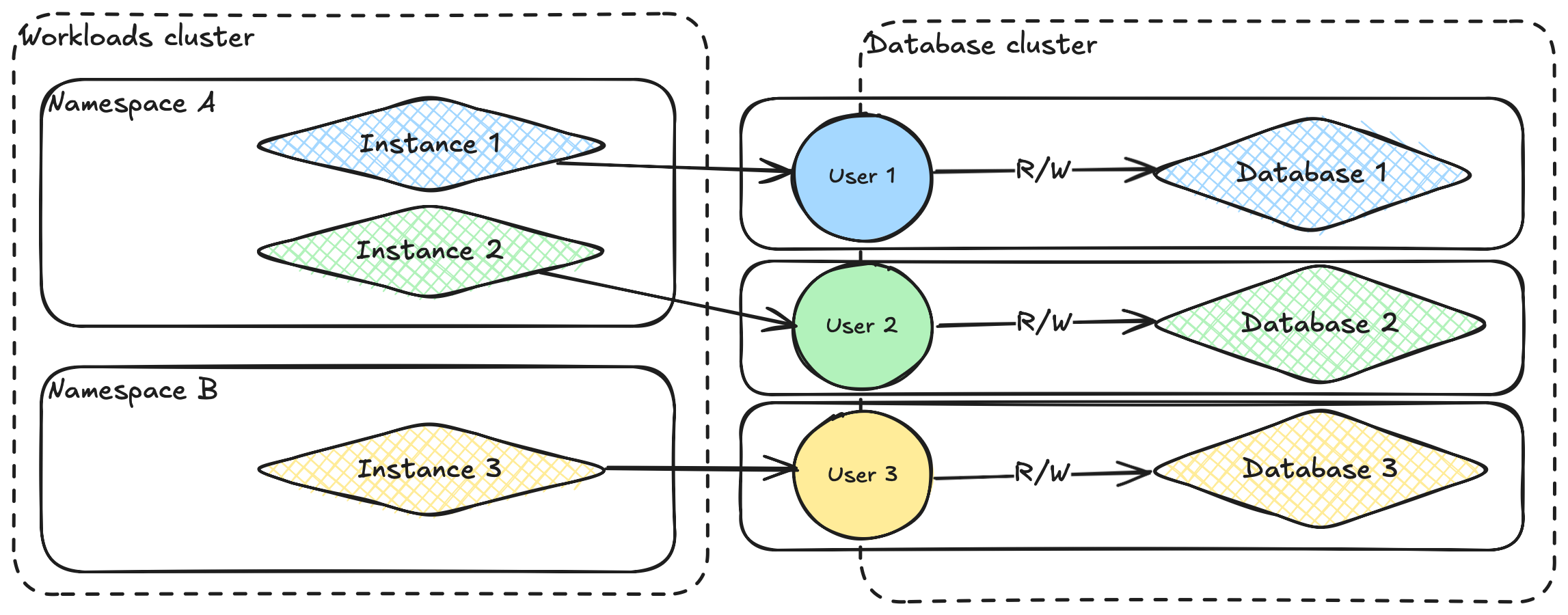
In the diagram above, dotted line represent shared resources while non-dotted lines represent boundaries between customers.
Encryption
Encryption is at the center of operating PKI software. Multiple layers of encryption occur in EVERTRUST Cloud :
At-rest encryption
-
The MongoDB database is configured to use MongoDB encryption at rest using an EVERTRUST-managed key, it encrypts data in the database engine on disk.
-
Backups are encrypted on disk using a key derived from the secret manager component.
In-memory encryption
Provided by EVERTRUST products, it ensures that sensitive data is never written in clear onto disk or in database. It is backed by a symmetric key, unique to each instance, provided by the secret manager
In-transit encryption
All data in transit is secured by TLS encryption. Details about the TLS encryption parameters can be found in ingress configuration.
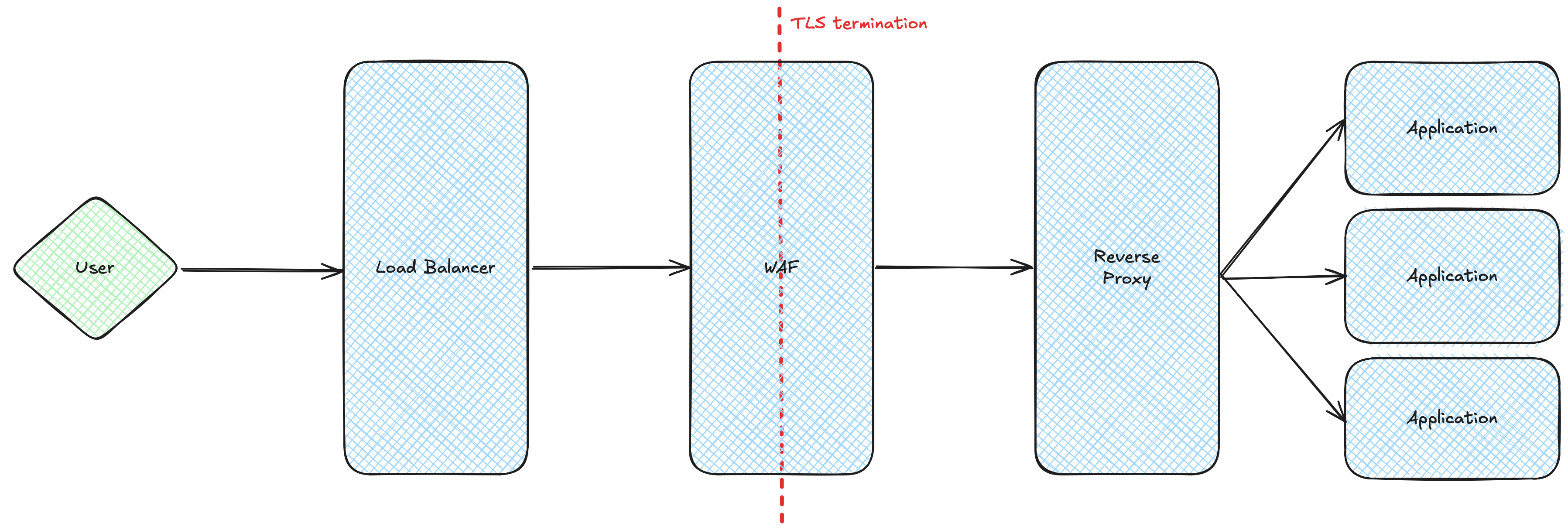
Request lifecycle
Each request in EVERTRUST Cloud goes through multiple steps before reaching the instance application. TLS termination occurs before in the WAF, so it can provide in-depth request analysis, such as :
-
decrease the attack surface by restricting allowed file types, headers, endpoints…
-
match and disrupt attack signatures
-
provide a DDoS protection