SCEP Profile
This section details how to configure the SCEP Profile
How to configure SCEP Profile
1. Log in to Horizon Administration Interface.
2. Access SCEP Profile from the drawer or card: .
3. Click on .
4. Fill in the mandatory fields.
SCEP Profile Specific Configuration
General
-
Name* (string input):
Enter a meaningful profile name. It must be unique for each profile. Horizon use the name to identify the profile. -
Enable (boolean):
Tells whether the profile is enabled or not. The default value is set to true. -
PKI Connector* (string select):
Select a PKI connector previously created. -
Authorize POST enrollment (boolean):
Enable scep enrollment routes with HTTP POST method. The defaults value is set to false. -
Authorization mode* (select):
SelectChallengemode to allow enrollment using a pre validated request containing a challenge,NDESmode to use challenge validation but allow automatic request creation by a user with enroll permissions,Authorizedto allow enrollment by a challenge containing credentials of a user with enroll permissions. In this mode, you can generate the credentials in the appropriate format by clicking on the shield icon. You will be asked to enter a username and password, then hit the 'Generate' button to display and/or copy the payload in the clipboard. SelectAuto Validationto use auto validation. -
Enable DN Whitelist* (boolean):
Tells whether the DN whitelist is enabled or not. The default value is set to false.
SCEP protocol parameters
-
Mode* (select):
Choose from the two modes RA or CA. The default value is set to RA. -
SCEP Authority* (select):
Select a previously created SCEP Authority. -
CAPS* (select):
Select a caps from the list. The default value is set to SHA. -
Encryption algorithm* (select):
Select an encryption algorithm from the list.-
Password policy (select):
Select a previously created password policy. It is used for the challenge generation.
-
Max Certificate per Holder Policy
-
Maximum (int):
When specified, define the maximum number of active certificates for a given holder. -
Behavior (select):
What behavior to have when the maximum number is reached:-
revoke the previous certificates.
-
reject the current request.
-
In order to allow renewal in reject behavior, one more certificate is allowed when the certificate being renewed is in its renewal period.
|
-
Revocation reason (select):
When the revoke behavior is selected, the revocation reason to revoke the certificate with.
Renewal management
-
Renewal period (finite duration):
Must be a valid finite duration.
Common configuration for profiles
Languages
You can add more languages by clicking .
-
Language* (select):
Select a language. Supported languages are:-
en: English
-
fr: French
-
-
Display Name (string input):
Enter a display name. This will be the localized name of this profile. -
Description (string input):
Enter a description. This will be displayed on the list view of the profiles.
You can delete the localization.
Grading Policies
You can select grading policies that will grade your certificate for a quick overview of its quality. For more information about the inner working of the grading policies in Horizon, please refer to the grading rules page.
Requests time to live
Configure the time your requests have before expiring.
| After expiration, requests are stored for an additional 30 days. This can be changed using configuration files. |
-
Enrollment request* (finite duration):
Must be a valid finite duration. The default value is set to seven days. -
Renewal request* (finite duration):
Must be a valid finite duration. The default value is set to seven days. -
Revocation request* (finite duration):
Must be a valid finite duration. The default value is set to seven days. -
Update request* (finite duration):
Must be a valid finite duration. The default value is set to seven days. -
Migration request* (finite duration):
Must be a valid finite duration. The default value is set to seven days. -
Recover request (finite duration):
Enabled on escrow: Must be a valid finite duration. The default value is set to seven days.
Constraints
-
Allowed email domains (string input):
Enter a valid regular expression that the inputted emails should match. This includes RFC822NAME and UPN SANs as well as the contact emailThis matches the domain of the email, not including anything before @. -
Allowed DNS domains (string input):
Enter a valid regular expression that the inputted domain should match.
Workflow
Auto-validation
Configure auto validation rules to avoid needing permissions configuration.
| A request permission must be available in order for the request to be created and then auto-validated. See workflows to modify request permissions. |
1. To enable auto-validation, switch the profile mode to auto-validation
2. Add rules that will be evaluated on each request. For more details, see the validation rules reference.
3. Add the threshold. This is the number of rules that must pass in order for the request to be validated.
Data source flow
Configure which data sources to execute and in which order.
1. Select a data source to execute first, and fill its inputs with a computation rule.
2. Add other data sources if needed. Each datasource input can use outputs from previously executed data sources.
3. All data sources output are available in computation rules throughout the certificate template and metadata.
Workflows builder
Configure custom rights for actions on this profile.
1. Select an authorization level for each workflow.
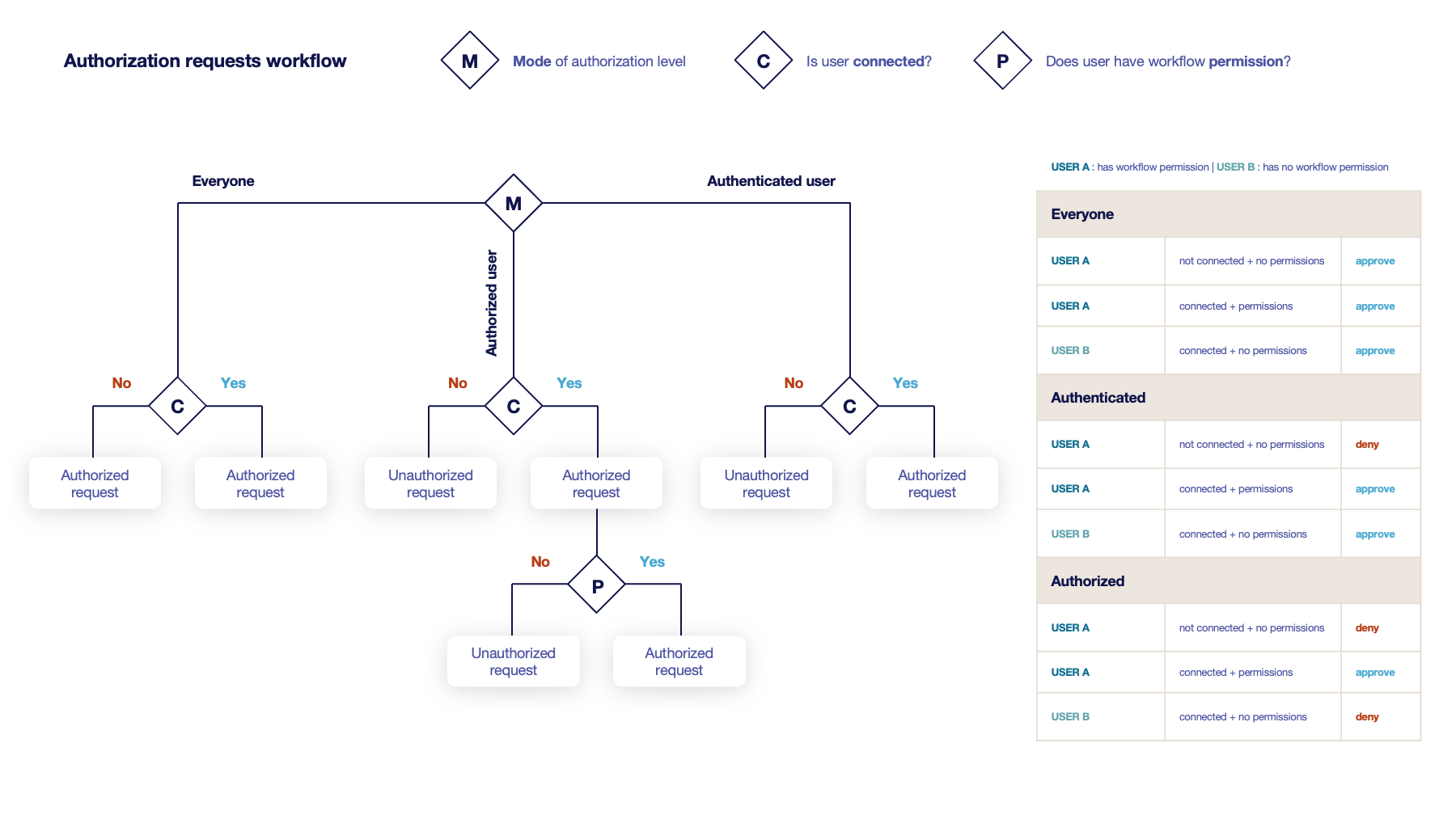
-
Everyone:
No authentication is required. -
Authenticated:
User has to be authenticated. -
Authorized:
User has to be authenticated and have an explicit authorizations.
2. Select an access level for identity providers.
You can remove the access level for an identity provider by clicking on 'x'.
Owner-related permissions
These permissions apply to the owners of a certificate (team or owner). An owner can always request the following actions, but this permission allows them to perform the action without validation.
-
Revoke (boolean):
Grant self revoke permission. The default value is set to false. -
Revoke (pop) (boolean):
Grant self revoke permission with owner being determined by Proof of Possession. This is used by horizon-cli. The default value is set to false. -
Update (boolean):
Grant self update permission. The default value is set to false. -
Update (pop) (boolean):
Grant self update permission with owner being determined by Proof of Possession. This is used by horizon-cli. The default value is set to false.
Certificate Template
This section details how to define a custom structure for the fields subject DN, SAN & extensions of the requested certificate in order to match the configuration on the PKI side.
| Defining a template will use the CSR to fill the available field. A CSR with unexpected fields will be rejected. Using a template also disables CSR Data Mapping. |
Subject DN composition
You can add more elements by clicking .
-
Element* (select):
Select an attribute from the elements list. -
Mandatory (boolean):
Should the element be mandatory. The default value is set to false. -
Editable by requester (boolean):
Tells whether the element should be editable by the requester. The default value is set to false. -
Editable by approver (boolean):
Tells whether the element should be editable by the approver. The default value is set to false. -
Default value (string input):
Set a default value to the element. -
Regex (regex):
Enter a regular expression that the element should match. -
Computation rule (Computation rule input):
Set the value of this element to the value of the evaluated computation rule. This value will override any other value including the user input and the default value.
You can remove an element by clicking the delete button or reorder (drag and drop)
the Subject DN template.
| When a template is defined, at least one mandatory Common Name must be added to the DN Elements. |
SAN composition
You can add more elements by clicking .
-
Element* (select):
Select an attribute from the element list. -
Editable by requester (boolean):
Tells whether the element should be editable by the requester. The default value is set to false. -
Editable by approver (boolean):
Tells whether the element should be editable by the approver. The default value is set to false. -
Minimum (int):
The minimum number of value that this SAN must have. -
Maximum (int):
The maximum number of value that this SAN must have. -
Regex (regex):
Enter a regular expression that the element should match. -
Computation rule (Computation rule input):
Set the value of this element to the value of the evaluated computation rule. This value will override any other value including the user input and the default value.
You can remove an element by clicking the delete button or reorder (drag and drop)
the SAN template.
Extensions
You can add more elements by clicking .
-
Element* (select):
Select an attribute from the elements list. -
Mandatory (boolean):
Should the element be mandatory. The default value is set to false. -
Editable by requester (boolean):
Tells whether the element should be editable by the requester. The default value is set to false. -
Editable by approver (boolean):
Tells whether the element should be editable by the approver. The default value is set to false. -
Default value (string input):
Set a default value to the element. -
Computation rule (Computation rule input):
Set the value of this element to the value of the evaluated computation rule. This value will override any other value including the user input and the default value.
You can remove an element by clicking the delete button or reorder (drag and drop)
the Extensions template.
| When adding a SAN, a DN element or an Extension and making it mandatory, make sure to either give it a default value or a computation rule or make it editable, otherwise the template will be unusable. |
Certificate Metadata
This section details how to define a custom structure for the labels, ownership policy and technical metadata, allowing certificates to hold rich information.
Labels
You can add more labels by clicking .
-
Name (select):
Select a preexisting label. -
Mandatory (boolean):
Should the label be mandatory. The default value is set to false. -
Editable by requester (boolean):
Tells whether the label should be editable by the requester. The default value is set to false. -
Editable by approver (boolean):
Tells whether the label should be editable by the approver. The default value is set to false. -
Default value (string input):
Set a default value to the label. -
Label value restriction
-
Whitelist (string input multiple):
The label value will have to be in the whitelist. Open the popup, enter the label value and press "enter" to add this value to the accepted value list. An empty whitelist means no restriction. -
Suggestions (string input multiple):
Add suggestions that will be displayed to the user. The user will be able to choose one of these values or enter its own. Open the popup, enter your suggestions and press enter to add this value to the suggestions. An empty suggestions list means no restriction. -
Regex (regex):
The label value will have to match the regex. Open the popup, enter the regular expression and click on the submit button to set the regex. An empty regex means no restrictions.
-
-
Computation rule (Computation rule input):
Set the value of this label to the value of the evaluated computation rule. This value will override any other value including the user input and the default value.
You can delete or reorder (drag and drop)
the label template.
Ownership policy
-
Owner
-
Mandatory (boolean):
Specify if the certificate’s owner is mandatory when submitting a request. -
Editable by requester (boolean):
Specify if the certificate’s owner can be overridden by the requester when submitting a request. -
Editable by approver (boolean):
Specify if the certificate’s owner can be overridden by the requester when approving a request. -
Computation rule (Computation rule input):
Set the value of the owner to the value of the evaluated computation rule. This value will override any other value including the user input.
-
-
Contact email
-
Mandatory (boolean):
Specify if the certificate’s contact email is mandatory when submitting a request. -
Editable by requester (boolean):
Specify if the certificate’s contact email can be overridden by the requester when submitting a request. -
Editable by approver (boolean):
Specify if the certificate’s contact email can be overridden by the requester when approving a request. -
Default contact email (string input):
Set a default contact email. This value must comply with the contact email restriction. -
Contact email restriction
-
Whitelist (string input multiple):
The contact email will have to be in the whitelist. Open the popup, enter the email and press "enter" to add this value to the accepted whitelist. An empty whitelist means no restriction. -
Regex (regex):
The contact email will have to match the regex. Open the popup, enter the regular expression and click on the submit button to set the regex. An empty regex means no restrictions.
-
-
Computation rule (Computation rule input):
Set the value of the contact email to the value of the evaluated computation rule. This value will override any other value including the user input and the default value.
-
-
Team
-
Mandatory (boolean):
Specify if the certificate’s team is mandatory when submitting a request. -
Editable by requester (boolean):
Specify if the certificate’s team can be overridden by the requester when submitting a request. -
Editable by approver (boolean):
Specify if the certificate’s team can be overridden by the requester when approving a request. -
Default team (string input):
Set a default team. This value must comply with the team restriction. -
Team restriction
-
Whitelist (string input multiple):
The team will have to be in the whitelist. Enter the team and press "enter" to add this value to the accepted whitelist. An empty whitelist means no restriction. -
Regex (regex):
The team will have to match the regex. Open the popup, enter the regular expression and click on the submit button to set the regex. An empty regex means no restrictions.
-
-
Computation rule (Computation rule input):
Set the value of the team to the value of the evaluated computation rule. This value will override any other value including the user input and the default value.
-
Metadata policy (overridable metadata)
| These metadata are technical metadata. They are used by Horizon or Third party connectors, updating them should be done with utmost care. |
| Metadata edition is not allowed on enroll. |
| Metadata edition is not available via the User Interface. It must be changed with API, using horizon-cli. |
You can allow the override of technical metadata by clicking .
-
Metadata* (select):
Select a metadata. -
Editable by requester (boolean):
Tells whether the metadata is editable by the requester. The default value is set to false. -
Editable by approver (boolean):
Tells whether the metadata is editable by the approver. The default value is set to false.
You can delete a metadata policy. This will not delete the metadata but will make it non editable.
Notifications
This section details how to configure notifications on certificate and request lifecycle events.
Certificate lifecycle notifications
Notifications are sent when one of the following event is triggered by a certificate:
Enrollment |
Revocation |
Expire |
Update |
Migrate |
Renew |
Request lifecycle notifications
Notifications are sent when one of the following event is triggered by an Enroll/Revocation/Update/Migrate/Renew request:
Submit |
Cancel |
Revoke |
Approve |
Pending |
| Submit request events are not triggered when the user has the permission to perform the action directly. |
5. Click on the save button.
You can edit , duplicate
or delete
the SCEP Profile.
|
You won’t be able to delete a SCEP Profile if this one is referenced somewhere else. |