jamf Pro
Introduction
This section details the jamf Pro integration with Horizon, used to enroll, renew and revoke certificates on jamf Pro managed devices.
This integration involves the following components:
-
jamf Pro server or Cloud instance
-
EverTrust Horizon
-
Devices to be enrolled
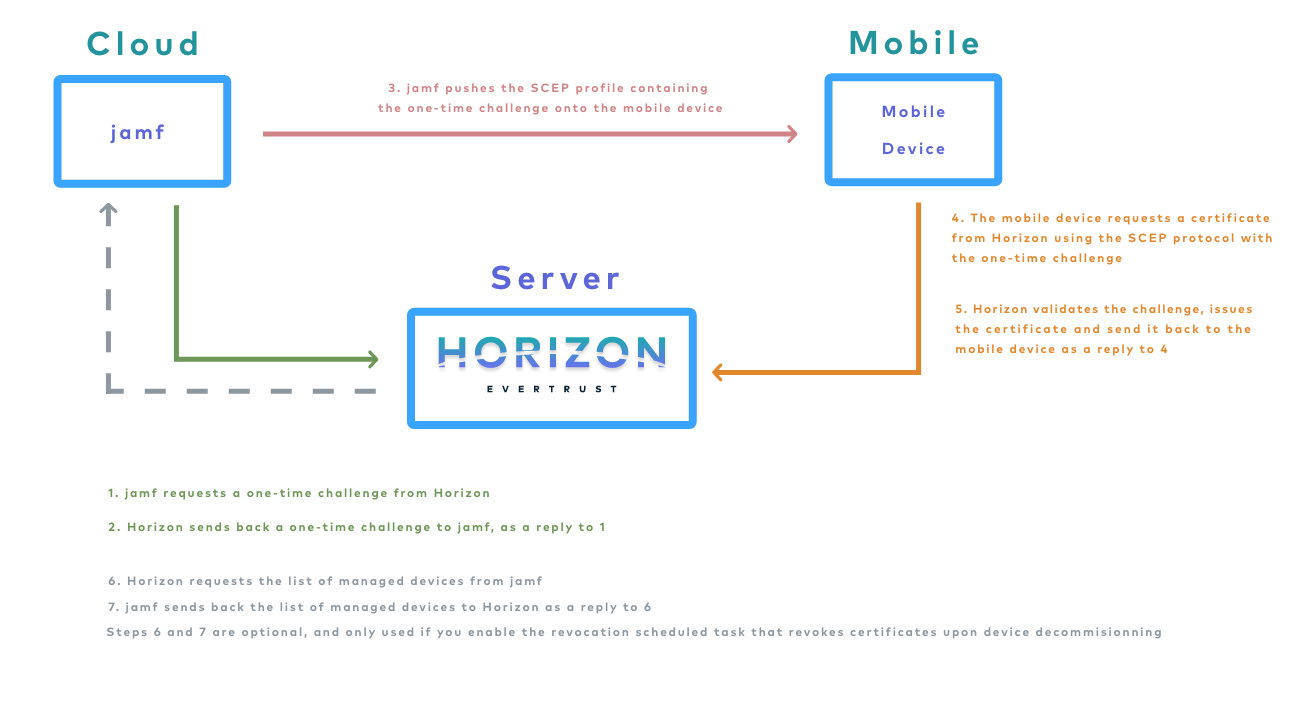
The diagram displays these components as well as the various flows involved in an enrollment.
Finally, this integration will require to setup, on Horizon side, the following elements:
-
a jamf Connector, which holds the configuration items required for Horizon to connect to jamf Pro
-
a jamf Profile, which holds the configuration items specifying how Horizon should issue certificates for the specified jamf Connector
-
a jamf Scheduled Task, which holds configuration items defining the scheduled task in charge of performing revocation upon decommissioning devices from jamf Pro. This is optional.
jamf Connector
This section details how to configure a jamf Connector.
Prerequisites
On Horizon side, you might need to set up a Proxy used to reach jamf Pro, if necessary.
On jamf Pro side, it is required to create a technical user for Horizon, and give it Auditor rights, so that Horizon will be able to list the devices managed by jamf Pro and thus be able to trigger certificate revocation upon decommissioning. Please follow the steps from the jamf Pro documentation. After performing these steps, you will be given the following information, required later:
-
a login
-
a password
How to configure jamf Connector
1. Log in to Horizon Administration Interface.
2. Access jamf Connector from the drawer or card: Third Parties > Jamf > Connectors.
3. Click on .
4. Fill the mandatory fields.
Connection
-
Name* (string input):
Enter a meaningful connector name. It must be unique for each connector. Horizon uses the name to identify the connector. -
Jamf endpoint URL* (string input):
Enter the URL pointing to the jamf deployment or the jamf Cloud instance. -
Login* (string input):
Enter the username created for Horizon in jamf. -
Password* (string input):
Enter the password associated with aforementioned username. -
Proxy (select):
The HTTP/HTTPS proxy used to reach jamf Pro, if any. -
Timeout (finite duration):
Set by default at 10 seconds. Must be a valid finite duration.
Actors management
These configuration elements mainly define the number of authorized interactions with the remote service on a defined period. For example, one needs to ensure that the remote service will not be contacted more than 5 times per 3 seconds. Throttle parallelism defines the number of times and Throttle duration the period of time. Therefore, on the above example, throttle parallelism would be set to 5 and throttle duration would be set to 3 seconds.
-
Throttle duration* (finite duration):
Set by default to 3 seconds. Must be a valid finite duration. -
Throttle parallelism* (int):
Set by default to 3.
5. Click on the save button.
You can update or delete
the jamf Connector.
|
You won’t be able to delete a jamf Connector if it is referenced in any other configuration element. |
jamf Profile
This section details how to configure a jamf Profile
Prerequisites
The SCEP Authority setup requires you to issue a certificate from the underlying PKI with the following characteristics:
-
to issue certificates for iOS:
-
the issuing CA should be the same as the one that will issue certificates through the PKI Connector that will be linked to the jamf Profile
-
the certificate key usages must include Digital Signature and Key Encipherment
-
the certificate must be issued as PKCS#12 and then imported into Horizon
-
-
to issue certificates for macOS:
-
the certificate should be self-signed
-
the certificate key usages must include Digital Signature and Key Encipherment
-
the certificate must be issued as PKCS#12 and then imported into Horizon
-
How to configure jamf Profile
1. Log in to Horizon Administration Interface.
2. Access jamf Profiles from the drawer or card: Third Parties > Jamf > Profiles.
3. Click on .
4. Fill the mandatory fields.
General
-
Name* (string input):
Enter a meaningful profile name. It must be unique for each profile. Horizon uses the name to identify the profile. As the name will be part of an URL, it is advised to use only lower case letters and dashes. -
Enabled (boolean):
Is the profile enabled or not. Set at true by default. -
jamf Connector (select):
Select a jamf connector previously created. -
PKI connector* (select):
Select a PKI Connector previously created. -
Max certificate per holder (int):
When specified, define the maximum number of active certificates for a given Holder.
Assets identification
-
DN field containing the device
UDID* (select):
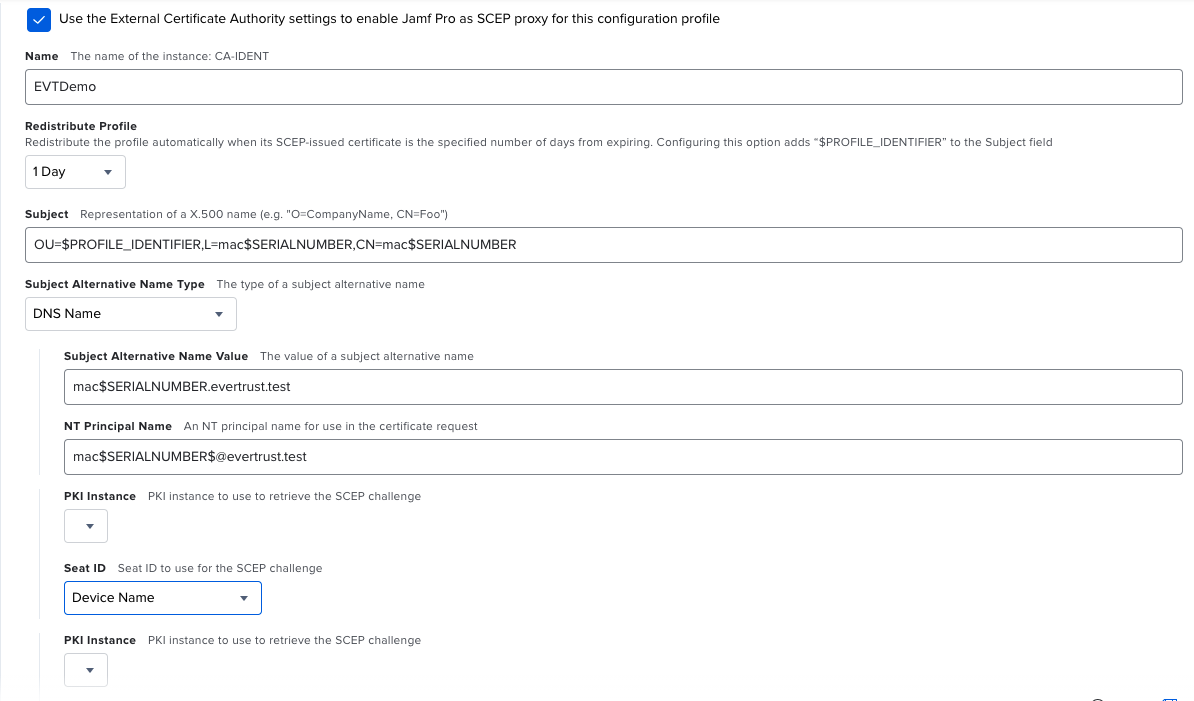
Field used to retrieve the Device ID. The selected field must be set to$UDID/$COMPUTERNAMEon jamf side, e.g. if you select "L", the configured Subject DN in the SCEP profile in jamf pro must then containL=$UDIDfor iOS orL=$COMPUTERNAMEfor macOS devices. This allows to use the automated revocation upon device decommissioning feature.
SCEP protocol parameters
-
Mode* (select):
Choose from the two modes RA or CA. To enroll certificates on iOS devices, select the RA mode. To enroll certificates on macOS, select the CA mode. -
SCEP Authority* (select):
Select a SCEP Authority previously created. See Prerequisites for details. -
CAPS (select):
Select one or many SCEP Capabilities from the list. If unsure, leave the default. -
Encryption algorithm* (select):
Select a SCEP Encryption Algorithm algorithms from the list. If unsure, leave the default. -
Password policy (select):
Choose from the password policy you might have previously created. If unsure, leave the default.
Renewal management
-
Renewal period (finite duration):
Must be in valid finite duration. -
Revocation on SCEP renew*: (boolean)
Should the expiring certificate be revoked upon SCEP renewal. Set by default at false. -
Revocation reason* (select):
Select the reason from the list. Available only if revocation on SCEP renew at true.
Self Permissions
-
Revoke (boolean):
Specify whether the certificate’s owner is authorized to revoke the certificate with no validation workflow. Set to false by default. -
Request Revoke (boolean):
Specify whether the certificate’s owner is authorized to request the revocation of the certificate. Set to false by default. -
Update (boolean):
Specify whether the certificate’s owner is authorized to update the certificate with no validation workflow. Set to false by default. -
Request Update (boolean):
Specify whether the certificate’s owner is authorized to request certificate’s update. Set to false by default.
You can further configure the profile using the Common configuration profile and Notification tabs.
5. Click on the save button.
You can update or delete
the jamf Profile .
|
You won’t be able to delete a jamf Profile if it is referenced somewhere else. |
Last Steps
The integration between jamf Pro and Horizon can be done in the following modes:
-
jamf Pro SCEP Proxy mode
-
iOS SCEP Profile
-
macOS SCEP Profile
-
macOS SCEP Profile with Proxy
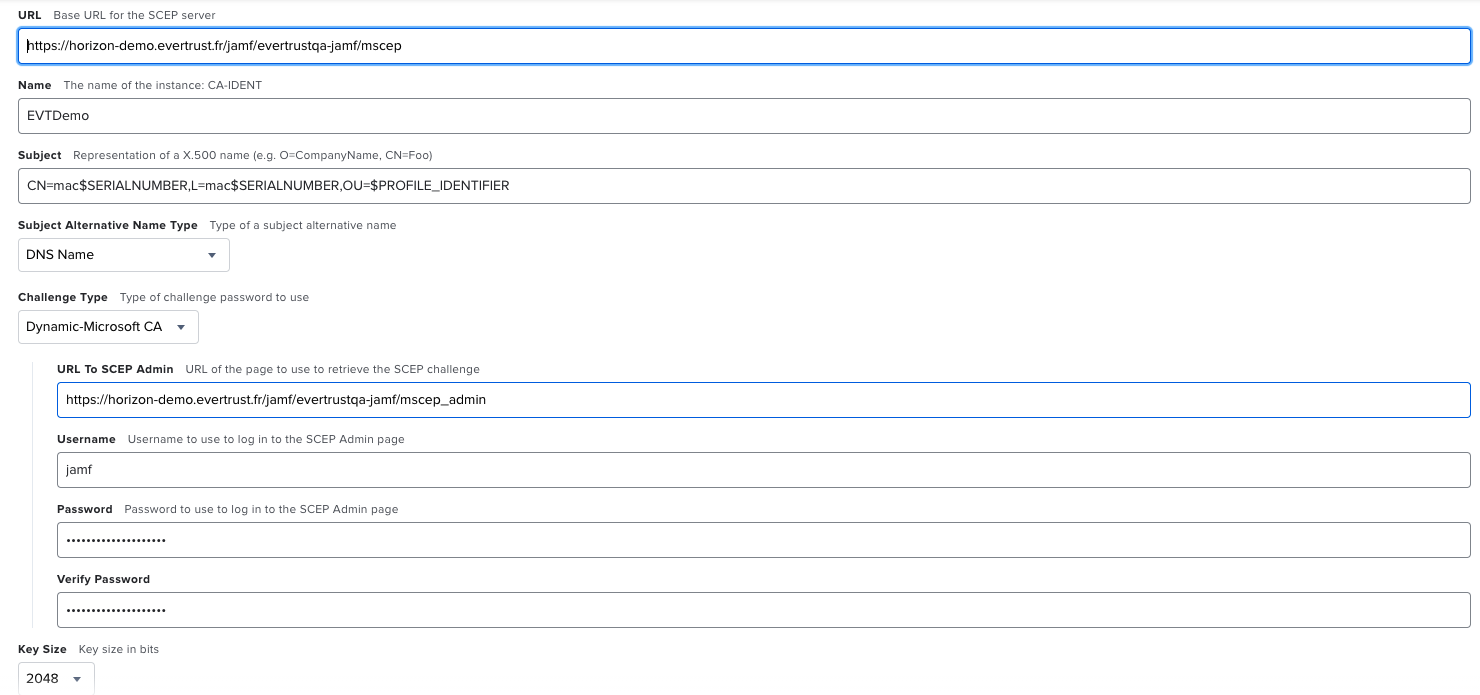
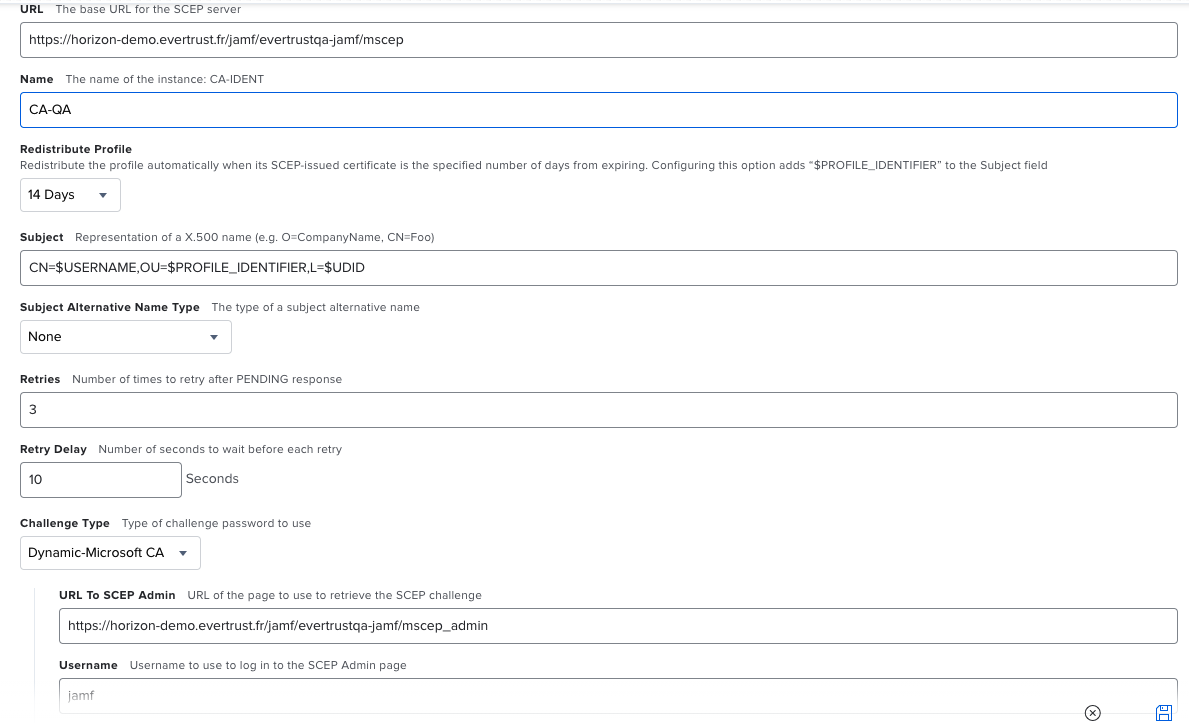
In all these modes, the Challenge type to use on jamf Pro side is Dynamic-Microsoft CA, and you should point to the corresponding mscep and mscep_admin URI on Horizon side, that can be found in the jamf Profile after it has been created.
jamf Scheduled Tasks
This section details how to schedule tasks that will run periodically on your jamf profiles, in order to manage automatic revocation upon device decommissioning.
How to configure jamf Scheduled Tasks
1. Log in to Horizon Administration Interface.
2. Access jamf Scheduled Tasks from the drawer or card: Third Parties > jamf > Scheduled Tasks.
3. Click on .
4. Fill the mandatory fields.
-
Enabled (boolean):
Tells whether the Scheduled task should be enabled. Set by default at true. -
jamf Profile* (select):
Select a jamf profile previously created. -
Target Connector* (select):
Select an jamf connector previously created. -
Cron scheduling (cron expression):
Set to every 5 hours by default. -
Revoke (boolean):
Set to false by default. If true, Horizon will revoke any certificate associated to a device that has been deleted from Azure AD (and hence decommissioned). -
Dry run (boolean):
If enabled, revocation actions will not be performed. Instead, a message will be logged, explaining what would have been done.
5. Click on the save button.
You can run or update
or delete
the Scheduled Tasks.